RECOMMENDATIONS
In this section we will recommend different actions to take either in security, deployment, processes, and infrastructure, among others:
Security
FOR MANAGERS AND OPERATION:
The following is a list of minimum activities to be performed on the system configuration:
1. Change the default admin password.
It is changed from the properties file attached to each node, setting the property admin.password=<password>
2. **Verify that the environment uses https (yes, the little padlock).
If you are a user please request it for your entity. If you are an administrator using Let’s Encrypt you can generate the certificate for free and using Cerbot you can renew it. If your province already has certificates with more validations, use those ones.
3. Do not leave any ports open to your server other than 443.
In this link , there is a quick guide on how to manage the firewall on the public server.
4.*Configure the Recaptcha from the properties file, setting the following properties:
- google.recaptcha.enable=true
- google.recaptcha.secret.key=<value obtained from the google administration console>
- google.recaptcha.site.key=<value obtained from the google administration console>
5. *Configure the two-factor authentication and notify users to activate it.
The configuration is done by setting the following properties
- Enable the app.feature.HABILITAR_2FA=true property
- Set an encryption key in the auth.2fa.password=encriptar property used to generate the two-factor authentication, it has to be the same in all nodes and not be changed once set.
6. Change the token.secret=<value> property to another key.
This key is used to set up the session token. If the default one is used, it is easier for a hacker to steal a person’s access.
7. Use different user types and passwords, and manage roles in database access.
While the application needs permissions on the main schema, limit access to other apps over access to the main schema, use views to restrict actions and any other mechanism you see fit.
8. Have your environments audited by security experts outside your organization:
Also, request tests of penetration, vulnerability analysis, code, libraries used, etc.
* Why do we recommend this? A weak password can be hacked using brute force in minutes. O copiar imagen y referenciar https://www.lymecsd.org/domain/154
* The fact that a page does not use a certificate means that the communication between ends (user and server) can be read. On the other hand, the domain being accessed is validated (according to the validation provided by the certificate).
FOR USERS:
1. Enable two-factor authentication. This is important because your username and password are easy to guess by a hacker trying combinations, and access to the system implies access to patients and depending on your role, access to sensitive information too.
To configure the two-factor authentication, you must enter your profile and there select the option: Enable two-factor authentication (if it does not appear, your entity does not have it enabled and you must request it).
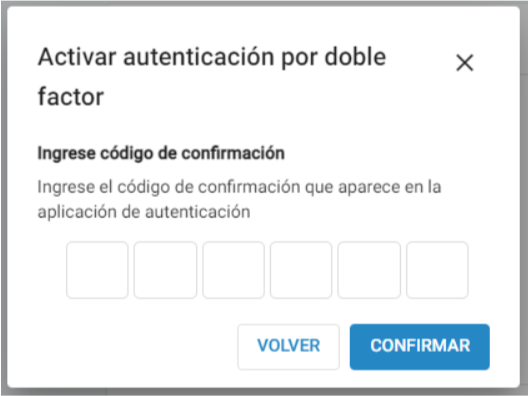
After clicking on this option it opens a dialog with a QR code and an alphanumeric code. These are the 2 options for setting up 2FA on the user’s mobile phone. Both options can be loaded in applications such as Google Authenticator or FreeOTP. Once loaded on the mobile phone, a 6-digit code can be obtained, which is reloaded every 30 seconds.

In the dialog, when going to the next step, the user is asked to enter this code. After pressing “Confirm”, it is verified that the code is valid (both in length and value), and then 2FA is activated for the user. If this 6-digit code is not entered correctly, 2FA will not be activated.
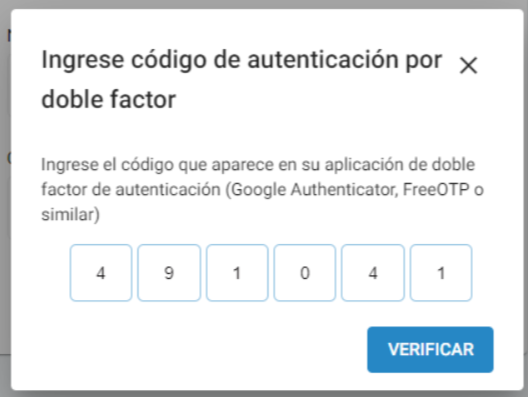
Once the two-factor authentication is activated, the next time the user logs in he/she will have to enter the username, password and also a 6-digit code for the two-factor authentication that appears on the mobile phone.
2. Verify that your login page uses a padlock, if not, do not use the system. Verify that the URL is valid, although the padlock makes certain verifications and encrypts the communication, maybe you entered another URL that is the same and someone wants to use it to get your information.
3. Change your password periodically. It is necessary because if someone is trying to get it, it will be more complicated.
4. When you log in, check when was your last access. This information is there so you can check if someone has used your account.
